第四届全国网络空间安全技术大赛CSTC
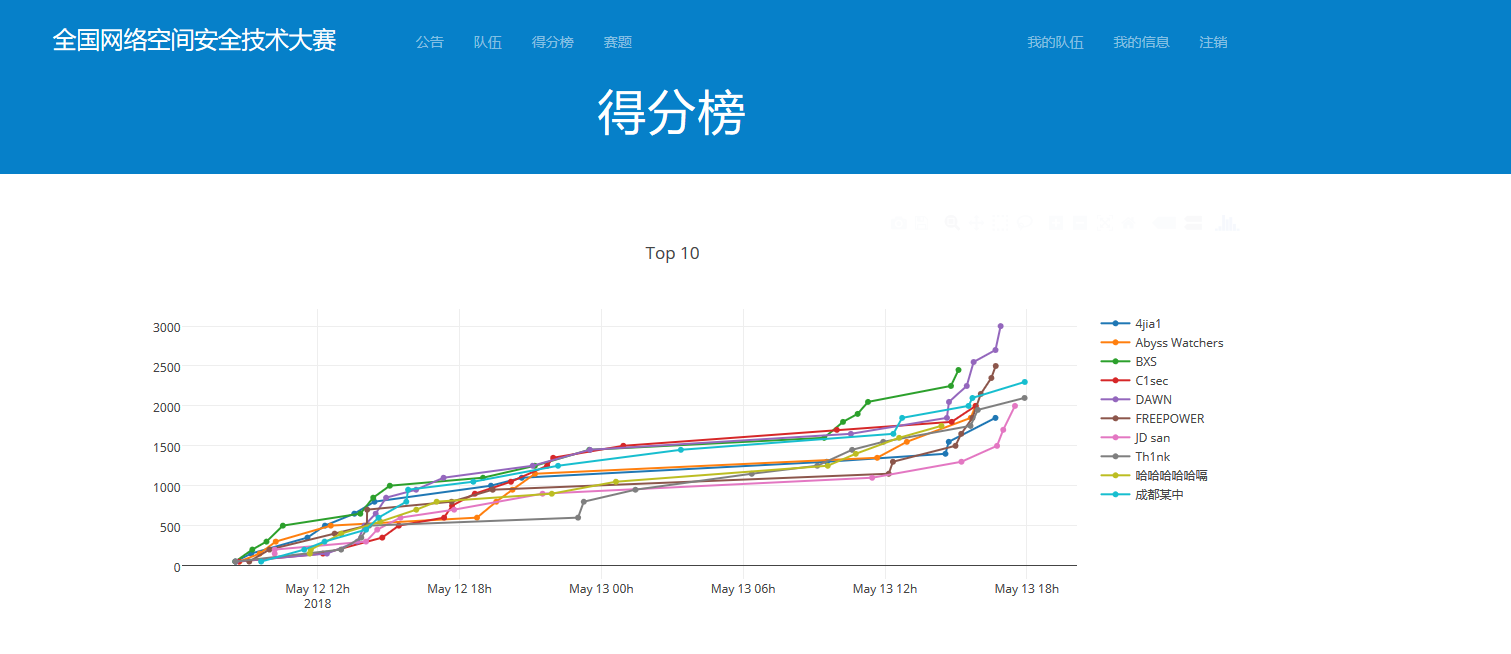
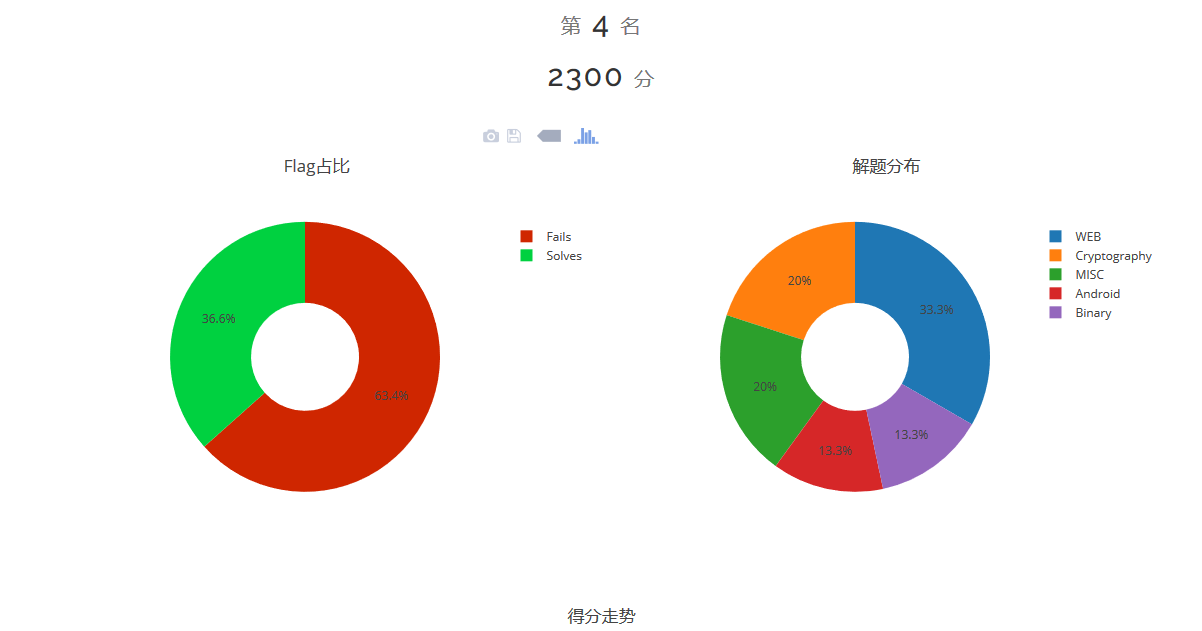
首先感谢我队两位师傅带我,给师傅们端了两天水拿了第四名
下面发的wp其中有一些是师傅们做的我理解了也一并记录了
RE1
拿到一个pyc,反编译成py,题目如下
1 | # Embedded file name: reverse.py |
由于加密的string前10位不变,所以爆破rc4的密钥就行
爆破脚本如下
1 | # Embedded file name: reverse.py |
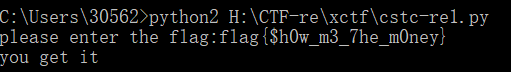
得到rc4密钥Flag也就出来了
RE2
首先是对输入有限制
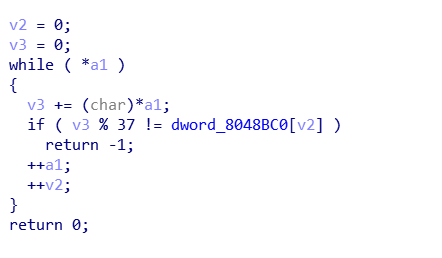
然后升序排列
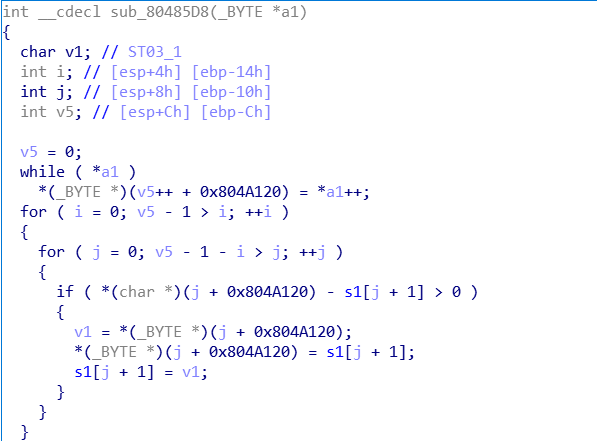
然后是循环(i+1,i+1*i+2)字符互换后做一个改了表的base64加密
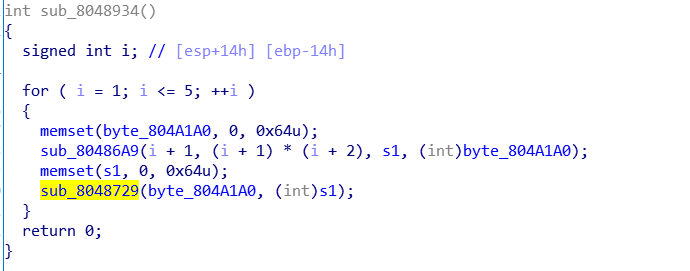
最后和q3HizxD4s1D2ztLJCZfhwuvoEMLeEgPlEK1imM0ZEM9dmKnyD3H6qurABt0=比较
flag{Hel10~Kitty }
MISC1
binwalk提出来一个txt,内容是base64隐写
flag{Ba5e_640Five}
RSA2
相关明文攻击,原理链接https://ctf-wiki.github.io/ctf-wiki/crypto/asymmetric/rsa/rsa_coppersmith_attack/
链接里的脚本数据改下就能直接用
M1≡aM2+b 有这种情况就可以用这个方法
flag{I_Lov5_RSA_Rel6te7_me8sagE_aTTack}
BLOCK
padding oracle attack 原理链接http://www.freebuf.com/articles/database/151167.html
解题脚本
1 | from pwn import * |
RSA
e和phi(n)不互素系列
import gmpy2
p = 111052706592359766492182549474994387389169491981939276489132990221393430874991652628482505832745103981784837665110819809096264457329836670397000634684595709283710756727662219358743235400779394350023790569023369287367240988429777113514012101219956479046699448481988253039282406274512111898037689623723478951613
q = 146182161315365079136034892629243958871460254472263352847680359868694597466935352294806409849433942550149005978761759458977642785950171998444382137410141550212657953776734166481126376675282041461924529145282451064083351825934453414726557476469773468589060088164379979035597652907191236468744400214917268039573
e = 200
c = 7797067792814175554801975939092864905908878472965854967525218347636721153564161093453344819975650594936628697646242713415817737235328825333281389820202851500260665233910426103904874575463134970160306453553794787674331367563821223358610113031883172742577264334021835304931484604571485957116313097395143177603380107508691261081725629713443494783479897404175199621026515502716868988672289887933681890547568860707175288422275073767747544353536862473367590288531216644146154729962448906402712219657000812226637887827912541098992158458173920228864293993030475885461755767069329678218760943185942331149777258713727459739405
N = p q
phi = (p-1)(q-1)
#gmpy2.gcd(e,phi) is mpz(8)
d = gmpy2.invert(25, phi/8)
p8 = gmpy2.powmod(c, d, N)
p = gmpy2.iroot(p8, 8)[0]
from Crypto.Util.number import long_to_bytes
print long_to_bytes(p)
总结
谢谢师傅带飞。。。
记得美亚柏科比赛的时候也是dawn第一名,PWN爷爷真是你爷爷系列: )
也许要找个机会入门pwn了8
