i-soonctf2019
[TOC]
Re
crackme
SM4算法,密钥为where_are_u_now?,密文经过魔改base64编码后进行对比验证。
求SM4密文脚本
1 | b64 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' |
然后SM4解密得flag
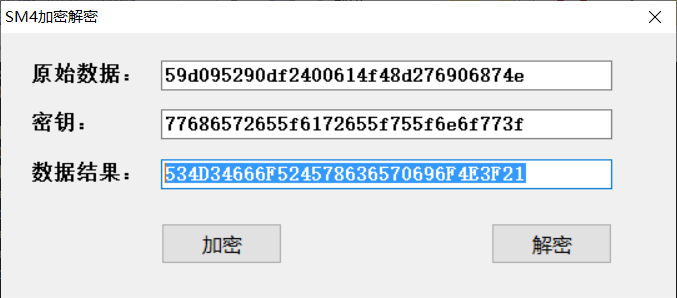
flag:SM4foRExcepioN?!
Easy_Encryption
1 | v3=[0x20,0x1F,0x1E,0x1D,0x1C,0x1B,0x1A,0x19,0x18,0x17,0x16,0x15,0x14,0x13,0x12,0x11, |
flag:umpnineissogood
game
1 | flag='4693641762894685722843556137219876255986' |
flag:KDEEIFGKIJ@AFGEJAEF@FDKADFGIJFA@FDE@JG@J
